JOTS v25n2 - Ideas
IDEAS
1. Rethinking the Issues of International Technology Transfer
by Ochieng Fred Walumbwa
Technology transfer has become a hot topic in business, industry, nongovernmental organizations, governments, and academia in the past several years ( Baker, David, & Soucy, 1995 ; Johnson, Gatz, & Hicks, 1997 ). With an increase in the speed of technology transfer, especially from the West to the developing world, issues of technology transfer demand special attention. There is a need to develop a universally accepted view and definition of technology transfer by integrating the various models. Such an integrated model would include sociocultural, economic, and political factors pertinent to the adoption and diffusion process. This article draws upon the existing definitions, views, and models of technology transfer to provide a conceptual model of international technology transfer that encompasses sociocultural, economic, and political factors that bear upon the adoption and diffusion of technology.
Various definitions of technology transfer exist. Williams and Gibson ( 1990 ) defined technology transfer as the moving of ideas from a research laboratory to the marketplace. Thus, technology transfer is an exchange of technical information between the research and development workers who innovate and the end users ( Rogers, 1995 ). The problem with these definitions is that they are too academic. They ignore the environment and tend to assume that once proper channels of communication are in place, transfer and diffusion should occur. While these definitions focus on technology as the core, they also neglect other important elements, such as sociocultural, economic, and political environments that impact technology transfer. An inclusive definition of technology transfer should include the transfer item; the developer of the technology; various channels to accomplish it, including communication; and the end users ( Market, 1993 ).
Leonard-Barton ( 1990 ) classified technology transfer into two generic rhetorical situations: point-to-point and diffusion. Point-to-point implies that a source develops an innovation for a highly specified purpose to a known audience user. Diffusion suggests that a source develops an innovation for a more general audience user whose purpose may or may not be clearly known. Unfortunately, most of the technology transfers take this latter form of diffusion.
The Model
The conceptual model of technology transfer (see Figure 1) has three broad categories surrounding the core technology: (a) developmental stage, (b) implementation process, and (c) diffusion. Technology transfer in this model is a cyclical rather than a linear process whereby the developers of the new technology collaborate with other forces of transfer, including the end users. This arrangement is important because it gives the developer an opportunity to assess future strengths, weaknesses, opportunities, and threats that might enhance or inhibit successful transfer. This way, the developer is able to apply appropriate strategies for implementation and diffusion of the new technology.
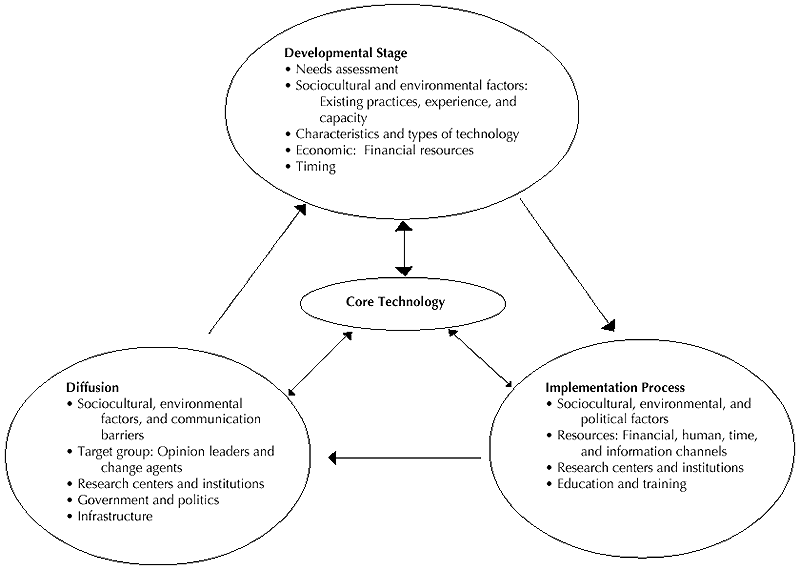
Figure 1. Conceptual model of technology transfer.
Technology transfer starts with a new idea, or a modification of an existing one ( Johnson et al., 1997 ). The double-sided arrows in the model infer that the variables in each of the three categories (developmental stage, implementation process, and diffusion) reciprocally affect the core technology being developed or modified. Some elements are found in more than one category of the model. This implies that these elements have multiple roles in the entire process of technology transfer. For example, an understanding of cultural, environmental, and political elements is important in the design stage to enable the developer of new or modified technology to find the "best fit." Technologies designed and developed with due consideration of the end users' needs and wants are likely to be adopted faster because many of the transfer barriers will have been addressed in the assessment. Culture, environment, and politics also play an important role not only in the transfer process, but also in diffusion ( Rogers, 1995 ).
The elements in the developmental stage are concerned with the intended end users of the new technology being developed or modified. These elements are specifically important in the design stage because they enable the developer to comprehend the culture of the intended local users, their economic capability, and their levels of willingness to use the new technology. A careful assessment of these elements should be a prerequisite for further steps in the transfer process. The implementation process elements are vehicles that facilitate technology transfer ( Jones, 1995 ; Parayil, 1992 ). Reynolds and Nadler ( 1993 ) argued that most international technology transfers fail at the implementation stage, perhaps because these elements are underutilized by the developers of new technology. According to the model, the development of human resources, such as capital and research institutions, are prerequisites for sustainable development of new technology. These institutions may be used as training centers for the end users to enhance their participation and ownership.
The diffusion process is the final stage in this model. At this stage individuals or groups of people decide whether or not to adopt and use the new technology. In most developing nations, given their traditional and cultural orientations, the role of the government and opinion leaders is paramount to successful diffusion of any new technology. Although infrastructure may not be under the control of the developer, it serves as a measure of the potentiality of the intended end users.
ELEMENTS OF TECHNOLOGY TRANSFER
Needs Assessment
Needs assessment is the first step in determining the needs and requirements of a specific country or society in which a new or modified technology is to be transferred. It is a systematic examination of conditions conducted for the purpose of identifying general strengths, weaknesses, and opportunities of the proposed technology in relation to the intended users. Needs assessment helps incorporate new technology into the prevailing physical and cultural environments of the receiving country ( Kofler & Meshkati, 1987 ). Savage and Sterry ( 1990 ) suggested that the following questions are important when conducting needs assessment: What will be the social costs? What kind of personnel, materials, tools, and knowledge will be needed to build, install, and operate the proposed new technology? What risks are associated with the proposed technology? What risks will the new or modified technology present to other physical environments? Answers to these questions are likely to provide solutions to what have been characterized as timing, cultural issues, communication obstacles, and problems of infrastructure ( Rogers, 1995 ).
Although needs assessment is important, it is often ineffective in the transfer of shortterm, fast-changing technologies-either due to changes in consumers' tastes or the speed of advancement of a particular technologysuch as computer software. Nonetheless, some sort of assessment in terms of consumer survey to determine product effectiveness is necessary. Obviously, needs assessment is a prerequisite for long-term technologies-technologies with lasting effects on the end users, for instance, educational, training, economic, and political policies.
Sociocultural and Environmental Factors
Sociocultural and environmental factors are embedded within the three categories of the model. Technology and culture impact one another; for instance, the introduction of new technology brings profound effects on a culture and people's beliefs, and some changes may even occur in the characteristics of community customs. Such changes are likely to have an influence on the transferability and/or diffusion of the technology. Therefore, it is imperative that we consider the role of sociocultural factors in the process of developing and transferring technology. In many instances, economics and political urgencies have been the driving principles of the development of the new technology-not the status of the end users. Consequently, disappointing results have ensued.
This model suggests that the practices and experiences of the intended users need to be considered in determining the appropriateness of new technology. Failure to consider cultural constraints, for instance, was reported to have contributed to the unsuccessful transfer of the American tractor to Russia ( Dalrymple, 1964 ). Socialist authorities gave more weight to political factors than to sociocultural factors of the Russian people. Technologies constructed within an existing culture have the greatest chances of success because the developers can use local institutional frameworks to identify problems and opportunities.
Characteristics and Types of Technology
The transfer of technology is greatly influenced by the nature and type of technology being transferred ( Rogers, 1995 ). Rogers ( 1995 ) identified five characteristics of innovation: relative advantage, compatibility, complexity, trialability, and observability (herein referred to as technology). Relative advantage refers to the degree to which the new technology is perceived to be much better compared to the existing technology. In the American cotton textile industry, the draper loom was easily transferred and diffused in the South in the 1960s because of perceived advantages such as labor savings ( Feller, 1974 ). By contrast, the perceived disadvantage of its high initial cost hindered its adoption in the North.
Compatibility is the degree to which the innovation is consistent with the values, needs, and experience of the recipients. For example, the role of societal norms and values was a major factor in the transfer and diffusion of technology in the American textile industry during the 19th century ( Jeremy, 1973 ). However, not all technology transfers need to be compatible or interactive with the local situations to be effectively adopted. For example, large innovations such as structural adjustment programs for developing nations require the bureaucratic procedures to get fully adopted. Complexity is the degree to which an innovation is perceived to be difficult. If technology is perceived to be complex and difficult by the end users, it may not be transferred easily. One example of this is the fast adoption of the "Sembradora" by the Mexicans despite the numerous advantages of the large tractors brought in by the Americans ( DeWalt, 1978 ). Trialability is the degree an innovation can be experimented on a regular basis before final adoption. This characteristic has been widely used in business organizations and in agriculture. Observability is based on the assumption that people are always motivated to learn new things. This concept explains the motive behind people's scrambling for new products or services whenever they are first introduced into the market.
Economic: Financial Resources
Technological transfers require high financial resources. In most cases they involve substantial amounts of capital that must be met by the recipient nations. Consequently, economic capabilities of the intended end users must be analyzed at the developmental stage. Such analysis provides an opportunity for the developer to design technology suitable for the local economy for sustainable development. Before a commitment is made about a new technology, the following questions should be asked ( Savage & Sterry, 1990 ): What will the proposed new technology cost to build or operate? How does that compare to the cost of the alternatives?
A new technology may have relative advantage and compatibility with the existing situations, but if the cost of maintenance and operation exceeds what the intended nation can afford, it becomes a burden. This is typical of some of the heavy and sophisticated machinery that was transferred to developing countries, especially in the field of agriculture, that the recipients could not maintain. Financial capabilities of technology recipient nations need to be given significant consideration if the process of technology transfer is to ensure continuity.
Timing
Although the concept of timing has received little attention in the technology transfer literature, it plays a very important role in an innovation's ability to progress ( Johnson et al., 1997 ; Rogers, 1995 ). As in any competitive environment, good timing is a valuable strategy for successful technology transfer. India's Green Revolution ( Parayil, 1992 ) is a classic example of new technology coming at the right time. The country had been undergoing a devastating drought so that any attempt to provide a solution was readily accepted.
Education, Training, and Human Resources
Education and training are major factors in the successful facilitation and implementation of technology transfer. The periods preceding independence in Africa witnessed a massive investment in education and training by the Western world. This was intended to develop and to train African human capacity capable of handling Western technologies. Further, it hoped to prepare African nationals to fill positions left by colonial masters. Indeed, this turned out to be a good strategy. Africans were able to successfully replace their former masters. Education and training probably provide the best vehicle to successful technology transfer. Educated and skilled people are more apt to use new technology than uneducated people since educated individuals adopt new approaches and alternative perspectives more readily. Therefore, some kind of education and skills are required to sustain the transfer of technology.
Communication Channels: Research Centers and Institutions
Communication is a process in which people share ideas ( Rogers, 1995 ). But that communication proceeds more readily between individuals with similar backgrounds in education, social status, beliefs, and language than between people of different backgrounds. Unfortunately, most transfers of technology involve people with different backgrounds, such as country, culture, discipline, or language. Therefore, learning to overcome communication barriers is a prerequisite for successful transfer of technology. The use of existing research centers and institutions may be a good strategy to facilitate the transfer of technology.
Target Group: Opinion Leaders and Change Agents
Change agents and opinion leaders are important elements in the transfer of technology. They are individuals who are knowledgeable in the social and political life of their respective societies. Many of them have been recognized by society for their past performance; hence, they are very influential. Research has indicated that people are more likely to listen and adopt ideas of those who are familiar to them than those they meet for the first time ( Rogers, 1995 ). Therefore, it is important to establish some form of connection with the local leaders who understand the culture in which the new technology is to be introduced.
Government and Politics
Politics plays a central role in the transfer of technology because it directly influences culture. Before the demise of the Communists, for example, Africa was divided politically into Eastern and Western blocks. During this period, the transfer of Western technologies in military, agriculture, and education reached most developing countries through the support of the local governments. Another classical example may be found in the Structural Adjustment Programs initiated by the International Monetary Fund. Lack of government commitment has been cited as a major cause of program failure in almost all communities where there have been failures. Since successful technology transfers require a coordinated approach between the receiving governments and the developers, we need to recognize the role that the state plays in the dissemination of new ideas, whether it is a democratically elected government or otherwise.
On the other hand, politics can be a hindrance to the transfer and diffusion of technology. This is especially true when the transfer has to go through bureaucratic processes that are likely to impede the transfer. Sometimes this is very costly, especially where administrative structures in infant stages encourage corrupt practices.
Infrastructure
Infrastructure includes such facilities as transportation, banking, housing, schools and colleges, research institutions, and telecommunication systems. Infrastructure is one of the obstacles to the transfer of technology in developing countries. The transfer of most new technologies requires laboratories, workshops, and even housing. Banks are needed to handle financial transactions for the running of daily activities within and without the new technology location. Colleges and research institutions are crucial to sustain and develop core personnel who can ensure continuity of the process of technology transfer.
Closure
Technology transfer is critical in today's complex world. There is an urgent need to address the pressing issues of culture and environment in the process of developing and transferring technology. This conceptual model has attempted to address these issues specifically in relation to other vital elements of technology transfer such as communication, needs assessment, power and politics, infrastructure, and the characteristics of technology. Like most models developed in this area, this model is restricted to the author's own experience and background. Consequently, the model may require modification to fit different experiences and backgrounds although the elements would remain the same. More studies are needed that integrate factors such as culture, politics, and physical environment in modeling technology transfer.
Ochieng Fred Walumbwa is a doctoral student in the Department of Human Resource Education at the University of Illinois.References
Backer , T. E., David, S. L., & Soucy, G. (1995). Introduction. In T. E. Backer, S. L. David, & G. Soucy (Eds.), Reviewing the behavioral science knowledge base on technology transfer (pp. 110). Rockville, MD: U.S. Department of Health and Human Services, Public Health Service, National Institutes of Health.
Dalrymple , D. G. (1964). The American tractor comes to Soviet agriculture: The transfer of a technology. Technology and Culture , 5(2), 191214.
DeWalt , B. R. (1978). Appropriate technology in rural Mexico: Antecedents and consequences of an indigenous peasant innovation. Technology and Culture , 19(1), 3252.
Feller , I. (1974). The diffusion and location of technological change in the American cotton-textile industry, 1890-1970. Technology and Culture , 15(4), 569593.
Jeremy , D. J. (1973). Innovation in American textile technology during the early 19th century. Technology and Culture , 14(1), 4076.
Johnson , S. D., Gatz, E. F., & Hicks, D. (1997). Expanding the content base of technology education: Technology transfer as a topic of study. Journal of Technology Education , 8(2), 3549 .
Jones , M. L. (1995). Management development: An African focus. In M. D. Mendenhall & G. Oddou (Eds.), Readings & cases in international human resource management (pp. 234247). Boston: South-Western College Publishing.
Kolfer , V. L., & Meshkati, N. (1987). Transfer of technology: Factors for success. In M. J. Marquardt (Ed.), Corporate culture: International HRD perspectives (pp. 7085). Alexandria, VA: American Society for Training and Development.
Leonard -Barton, D. (1990). Modes of technology transfer with organizations: Point-by-point versus diffusion . Boston: Harvard Business School, Division of Research.
Market , L. R. (1993). Contemporary technology: Innovations, issues, and perspectives. South Holland, IL: Goodheart-Wilcox .
Parayil , G. (1992). The green revolution in India: A case study of technological change. Technology and Culture , 33(4), 737756.
Reynolds , A., & Nadler, L. (1993). Globalization: The international HRD consultant and practitioner . Amherst, MA: Human Resource Development Press.
Rogers , E. M. (1995). Diffusion of innovations (4th ed.) . New York: Free Press.
Savage , E., & Sterry, L. (1990). A conceptual framework for technology education . Reston, VA: International Technology Education Association.
Williams , F., & Gibson, D. (1990). Technology transfer: A communication perspective . Newbury Park, CA: Sage.
2. Evolving Models of Technology Teacher Preparation
by William D. Paige
For years we have read articles, observed presentations at conferences, and heard reports of numerous research efforts concerning the shortage of teachers for technology education programs across the country ( Householder, 1993 ; Volk, 1997 ; Weston, 1997 ; Young-Hawkins, 1996 ). There are many reasons for the shortage of technology education teachers, and the problems are complex. This article attempts to provide an overview of one facet of this issue by first outlining the traditional way in which teachers have been prepared and licensed and/or certified to teach in the public school systems in the United States. Second, several alternative methods of obtaining teaching licensure and/or certification are presented, followed by some personal thoughts about these alternatives and the future of our profession.
Historically, the most common way to prepare for a career in teaching in any field of study has been to complete a four-year bachelor's degree program in education. This traditional college- and university-based teacher preparation program is based on the belief that "becoming a teacher requires several years of preservice professional training and supervised practical experience prior to assuming full-time teaching responsibility" ( Stoddart & Floden, 1995 ). According to Sullivan ( 1995 ), traditional teacher certification programs are usually characterized by a specified number of credit hours to be earned in (a) content area, (b) professional coursework, and (c) an internship. After the candidates successfully complete all requirements for the baccalaureate degree in education, the colleges or universities verify that they have met the minimum state licensing requirements. These state licenses and/or credential requirements signify to the public that people with either of these endorsements possess a level of professionalism and high standards and are at least minimally qualified to teach in our schools ( Sullivan, 1995 ).
Householder ( 1993 ) explained that many of today's teachers of technology education were and are being prepared in programs based on the traditional historical model of teacher preparation. One might question the wisdom of this approach when considering that the traditional process of teacher preparation has received much negative attention in the past decade. Specifically, reports from the National Commission on Excellence in Education's ( 1983 ) publication of A Nation at Risk , the Carnegie Task Force on Teaching as a Profession ( 1986 ), and the Holmes Group ( 1986 ) among others, have all raised questions about the quality of our education system, including the process of teacher preparation. Concern has been voiced regarding the declining average ability of students and the trend of more academically able students choosing careers other than teaching ( Schlechty & Vance, 1983 ). The recognition of the importance of quality teaching, the low college entrance test scores of those wanting to teach, and the reality of a future teacher shortage are among the factors that have led to numerous propositions demanding changes in higher education and proposals to reform the way teachers are prepared.
One of the proposals for reforming teacher education would require that teacher preparation programs be extended to five years. This proposal is based on the assumption that students in extended programs will take additional coursework in the subjects they are preparing to teach, resulting in an increase in their effectiveness as a teacher. Furthermore, it is believed that by extending the length of the program the status of the profession of teaching will be enhanced ( Hawley, 1992 ). Whether or not these assumptions are correct, or if extending the length of the programs will have any major impact on the profession, remains to be seen. Simply extending the length of time it takes to become a technology education teacher does not seem to do anything but compound the problem of the teacher shortage.
One model that could help eliminate the shortage of technology education teachers would be to provide an avenue for those persons who already hold a baccalaureate degree in a technology-related field to earn a teaching certificate by obtaining the necessary coursework in education without having to go through a full teacher education program. Such alternative certification programs were introduced in many states during the 1980s in response to the severe teacher shortage that existed primarily in the areas of math and science. Alternative certification programs were established to help alleviate the teacher shortages that existed in rural and urban schools ( Duhon-Haynes et al., 1996 ; Rubino et al., 1996 ; Rubino et al. 1994 ).These programs were established by school districts, boards of cooperative services, independent schools, institutions of higher education, state departments of education, and private foundations either independently or in concert with them.
Supporters of these alternative certification programs believe that individuals who demonstrate subject matter knowledge can learn to teach effectively. Typically, such programs begin with preparation in teaching methods and classroom management before the program participants enter the classroom to begin teaching. During their first year of teaching, participants are given support and guidance by a mentor/master teacher. Following this first year of teaching, the program participants usually return for additional coursework and preparation to fulfill any other requirements for licensure/certification.
One example of this model of alternative teacher preparation is a program at Christopher Newport University, which offers an alternative licensure program for people with an earned degree in liberal arts or science. For this program, the education courses have been re-sequenced so that the students take an entire semester of only education courses (18 credit hours). The following semester the students participate in an internship program and take an additional two courses (16 credit hours). At the end of the second semester, the program participants have completed all requirements for licensure. A review of this program found that although it worked, the program would have been better if a summer session had been added to ease the students' load during the year ( American Association of State Colleges and Universities [AASCU], 1995 ).
Table 1. Postbaccalaureate Programs in Technology Teacher Education
University
Program Name
Area
University of Central Arkansas Postbaccalaureate Teacher Licensure TE Central Connecticut St. Univ. Post-Graduate Certification Program TE Illinois State University Second Bachelor's Option IT Illinois State University (No Name) IT Northwestern St. Univ. of LA Alternate Certification IA ED Mankato State University Master of Arts in Teaching TE Jackson State University, MS Second Degree Program IA Central Missouri St. Univ. Post-Baccalaureate Teaching Cert. IA&T Southeast Missouri St. Univ. Certification-Only Program IT Montana State University Non-Degree Cert. only Program TE Western Montana College Certification only ITE Keene State College Postbaccalaureate Teach. Cert. TE Montclair State University Post BA Teacher Certification Prgm. TE California Univ. of PA Postbaccalaureate Certificate TE Oregon State University Professional Teacher Educ. Prgm. TE Southwestern OK St. Univ. Certification-Only Program TE Tennessee State University Postbaccalaureate Teacher Educ. T Old Dominion University Military Career Transition Program TE MS Education Licensure Program Fairmont State College Alternative Program TE The Tarleton Model of Accelerated Teaching (TMATE) is an alternative certification program operated by a consortium of school districts in Texas and Tarleton State University. Participants in this program take a block of 12 semester credits in teaching methodology, classroom management, and instructional design that includes practice teaching in an enrichment program for K8 students during summer school. In the fall they assume full-time teaching responsibilities under the guidance of a schoolbased mentor and a university supervisor. During this school year, the participants also attend a series of weekend seminars. The next summer session involves a post internship block that prepares them to take the licensure examination. In the eight years this program has operated, over 400 persons have successfully completed all requirements and 93% of those have been placed in teaching positions in rural schools ( AASCU, 1995 ).
In 1990, 48 states reported having alternative certification programs ( American Association of Colleges for Teacher Education [AACTE], 1990 ). Feistritzer ( 1992 ) reported that from 1985 to 1990 approximately 20,000 candidates were certified through alternative routes and that number had increased to 40,000 by 1992. The AACTE 1996 directory of postbaccalaureate programs lists 328 programs in colleges and universities for individuals with a bachelor's degree who want to earn a teaching license. Table 1 lists the schools from that directory that reported having a postbaccalaureate program in technology education, industrial technology education, or industrial arts education. Another beneficial source of names, addresses, and telephone numbers for each state's teacher certification personnel is the Manual on Certificators and the Preparation of Educational Personnel prepared annually by the National Association of State Directors of Teacher Education and Certification. Even though post-baccalaureate alternative certification programs may vary widely from state to state in content, specificity, structure, and base of organization, the typical alternative certification program has the following general characteristics:
- Uses a rigorous screening process to ensure the selection of talented, qualified teacher interns who are academically and personally competent.
- Provides high-quality pre- service training in methodology, classroom management, and human development.
- Consists of a structured, well-supervised induction period that includes guidance by a mentor teacher for the period of one year.
- Requires ongoing professional development, including seminars, workshops, and university course work, that addresses the specific needs of the teacher-intern.
- Follows up with post-internship training to ensure continued effective training ( Littleton & Holcomb, 1994 ).
Another alternative certification model provides an individual who already holds at least a bachelor's degree along with a teaching license/certificate in a subject area other than technology education an opportunity to obtain the requisite knowledge and experiences to teach technology. Householder ( 1993 ) indicated that "the British have been quite successful in using the in-service model to provide the experiences in technology that are needed to prepare primary and secondary teachers to implement technology in their national curriculum" ( p. 18 ).
An example of an American-based inservice program is South Carolina's Industrial Technology Education Add-On Certification Program. This program, which is funded by the State Department of Education, is in its fourth year of operation at both Clemson University and South Carolina State University. The program consists of 36 credit hours of technology education course work, taken over a three-year period, and is provided at no cost to the participants.
The program was designed to provide the participants with 12 semester credit hours in the spring and summer sessions, enabling them to obtain an out-of-field teaching license for the following school year to teach technology education. The participants then take 12 credit hours per year for each of the following two years, followed by area examination of the National Teachers Examination. Program participants are then fully certified to teach technology education in South Carolina's public schools.
Individuals who have at least a baccalaureate degree, who have had a successful career in business, industry, or the military, for example, and who are interested in teaching are another source of future technology education teachers. Providing these individuals an opportunity to complete the academic requirements for a teaching certificate and retrain for another career can help alleviate the present shortage of qualified personnel in our classrooms. Persons who have had positive life experiences and previous careers and who also have a strong desire to help youth as they grow, often become outstanding teachers. Simpson and Jackson ( 1997 ) wrote:
Teacher education candidates who know something about the complexities of life, who have grown through their nonacademic educational experiences-and perhaps their own difficulties in schooland who can share their insights with their colleagues and students may have important and relevant experience to contribute. Perhaps this experience explains why many second career and late entering teachers receive praise today for their ability to "relate to" all students. ( p. 161 )
Programs such as the Military Career Transition Program at Old Dominion University and the MS in Industrial/Technology Education at U. W. Stout are successful examples of re-training programs that are providing avenues for very talented individuals to become teachers of technology education.
One can only imagine exactly what the future holds for teacher education programs. What new avenues may be available for teacher education programs as new technology impacts the classroom? Many fundamental questions come to mind such as the following: Will the classrooms have four walls? Will the teacher be in the classroom with the students, in the same building, or even on the same university campus? Will they even be in the same state or country? With the use of today's technology, the answer to all of these questions is probably a resounding NO! Daugherty ( 1997 ) recently wrote:
A new day is dawning in technology teacher education. The preservice teachers in class today will most likely begin their teaching careers in the 21st century. Technology teacher education must enter the new millennium with new structures, new approaches, and a shared base of knowledge about teaching that the new professional technology teacher can apply in daily practice. Members of the profession must resolve themselves to developing new approaches to teacher training and the career development of teachers. The recruitment and selection of teachers is critically important worldwide, and the initial preparation of teachers and their continuing professional development are key factors in improving technology education at all levels. ( p. 52 )
Whether future teachers for technology education classrooms are prepared in traditional programs or gain certification through one of the various alternative programs that are presently available, they must be both technically and professionally competent. The use of assessment instruments such as Praxis Series can be used to help provide evidence of a person's professional and subject specific knowledge and skill. This type of documentation is essential in the licensure and certification process to maintain quality teachers in our technology education classrooms. Until the time comes that there is no longer a shortage of technology education teachers, we, as a responsible profession, must examine every possible avenue that will allow us to bring qualified people into our programs and prepare them for positions in our classrooms and laboratories. The alternative preparation programs outlined in this article admittedly have not eliminated the teacher shortage, but they have helped the situation by providing some outstanding technology education teachers in areas where there is a critical shortage. Providing opportunities through alternative preparation programs for people who are excited about learning and teaching technology education and share their enthusiasm with students will do nothing but enhance the overall future of our profession.
Dr. Paige is Professor in the Department of Technology and Human Resources Development at Clemson University, South Carolina. He is a Distinguished Service member and Trustee of the Gamma Tau Chapter .References
American Association of Colleges for Teacher Education. (1990). Teacher education policy in the states: A 50-state survey of legislative and administrative actions . Washington, DC: Author.
American Association of Colleges for Teacher Education. (1996). Alternative paths to teaching: A directory of postbaccalaureate programs (2nd ed.). Washington, DC: Author.
American Association of State Colleges and Universities. (1995). Changing course: Teacher education reform at state colleges and universities . Washington, DC: Author.
Carnegie Task Force on Teaching as a Profession. (1986). A nation prepared: Teachers for the 21st century . New York: Author.
Daugherty , M. K. (1997). The future of technology teacher education: A faculty vision. The Journal of Technology Studies , 23(1), 4753 .
Duhon -Haynes, G., & Others. (1996). Post-baccalaureate teacher certification programs: Strategies for enhancement, improvement, and peaceful co-existence with traditional teacher certification programs . (ERIC Document Reproduction Service No. 404 334)
Feistritzer , E. (1992). Who wants to teach? Washington, DC: National Center for Education Information.
Hawley , W. D. (1992). The alternative certification of teachers (Teacher Education Monograph No. 14). (ERIC Document Reproduction Service No. ED 351 334)
Holmes Group. (1986). Tomorrow's teachers: A report of the Holmes Group . East Lansing, MI: Author.
Householder , D. L. (1993). Technology teacher education: Status and prospect. The Journal of Technology Studies , 19(1), 1419.
Littleton , M., & Holcomb, J. (1994). New routes to the classroom. The American School Board JournalM , 181(4), 3739.
National Association of State Directors of Teacher Education and Certification. (1996-1997). Manual on certificators and the preparation of educational personnel . Dubuque, IA: Author.
National Commission on Excellence in Education. (1983). A nation at risk . Washington, DC: U.S. Department of Education.
Rubino , N., & Others. (1994). Alternative teacher certification: An avenue for quality and diversity in public education . (ERIC Document Reproduction Service No. ED 382 609)
Schlechty , P. C., & Vance, V. S. (1983). Recruitment, selection, and retention: The shape of the teaching force. Elementary School Journal , 83, 469487.
Simpson , D. J., & Jackson, M. J. B. (1997). Educational reform: A Deweyan perspective . New York: Garland.
Stoddart , T., & Floden, R. E. (1995). Traditional and alternative routes to teacher certification: Issues, assumptions, and misconceptions (Issue Paper 95-2). Washington, DC: U.S. Department of Education, National Center for Research on Teacher Learning.
Sullivan , M. E. (1995). Rural settings: One approach to meeting teacher staffing needs via alternative certification . (ERIC Document Reproduction Service No. ED 381 318)
Volk , K. S. (1997). Going, going, gone? Recent trends in technology teacher education programs. Journal of Technology Education , 8(2), 6771 .
Weston , S. (1997). Teacher shortage-Supply and demand. The Technology Teacher, , 57(1), 6-9.
Young -Hawkins, L. (1996). Recruiting technology education teachers: Broadening the pool of talent. The Technology Teacher , 56(2), 2630.
3. A Collaborative Approach for Redefining a Program
by Brenda L. Wey and Mark Estepp
Graduate education plays a vital role in the overall mission of comprehensive universities. A quality graduate program enhances faculty opportunities to become involved in research projects, provides research and teaching opportunities for graduate students, and raises the overall prestige of the department. An active graduate program enlivens the department by allowing close interaction between faculty and students on an advanced level. Graduate level courses allow curricular experimentation and implementation of a wide variety of teaching techniques that are sometimes difficult to apply at the undergraduate level.
Curricular change is essential to the continued success of all academic programs, but particularly essential to technologyrelated disciplines. Falling behind in curriculum matters is often a matter of months in technical fields, where in other disciplines it is a matter of years.
However, curricular change should not be entered into lightly. The process should be designed to be thought provoking and offer the opportunity to gain insights, information, and ideas from fellow colleagues and professionals from industry. This documents the challenges and processes involved when a collaborative approach is used to develop and implement curriculum change. It offers perspectives on creative collaborations used to revise a graduate curriculum and shares the rewards of this collaboration beyond the scope of just curriculum changes. It creates a cooperative and revitalized commitment within the department to graduate education.
The Setting
Appalachian State University was recognized as one of the top industrial arts programs in the southeast during the 1960s and 1970s. During the 1980s the department changed its emphasis from preparing students for careers in teaching to preparing students for professions in industry and business at both the graduate and undergraduate levels. This change reflected a national trend based on student demand for nonteaching industrial technology degrees. The undergraduate program evolved from a degree in industrial arts at the undergraduate level to technology education and a degree in industrial technology with concentrations in appropriate technology, construction, electronic technology, graphic arts and imaging technology, industrial drafting and design, manufacturing technology, and technical photography.
The graduate curriculum remained basically the same through the 70s and early 80s. Changes that occurred in the mid 80s added a concentration in industrial technology for nonteaching majors and included a revision of core classes.
Program Review
In 1992 the graduate program was evaluated in accordance with the university's graduate program review process. The Graduate School dean appointed a review committee that included a mix of faculty from other departments and the Department of Technology. The committee collected and summarized information from interviews, surveys, and graduate records such as applicant information, students' scores for admission, graduation rates, and enrollment data. The review process included sending surveys to all graduate students currently in the program, all alumni who graduated in the previous five years, and all graduate faculty in the Department of Technology. Selected graduate students and alumni met to discuss their views on the graduate program. This meeting was conducted by committee members from other departments; technology faculty were not present.
These efforts resulted in a comprehensive evaluation of the department's graduate curriculum. It identified the strengths and weaknesses of the program. Strengths included the faculty, flexibility in program design, opportunity for advanced skill development, and the quality of experiences in the graduate assistantship. Recommendations included the restructuring of graduate courses to address the following concerns:
- Develop a technology research course. Nonteaching technology majors needed more emphasis on experimental and scientific research specifically related to technology applications.
- Delete graduate courses in specific technical areas that had low enrollment.
- Add new courses that reflect current technology applications appropriate for all technical areas.
- Develop concentrations for the industrial technology major.
This review process involved the collaboration of the departmental graduate faculty, students, and alumni, and faculty from other departments. The report was well received throughout campus, and it helped in the recognition of the purposes and goals for the Department of Technology on a universitywide basis.
Revising the Graduate Curriculum
Major revisions to the graduate program were completed during the 1997 spring semester. The new program went into effect during the 1997 fall semester. The curriculum changes were the result of the efforts and hard work of many individuals. Major components of this effort were the graduate program review at the university level; a selfstudy by students, faculty, and administrators in the department and college; alumni evaluations of the program; and discussions with a network of professionals from other universities and industry.
Goals for Curriculum Change
Critical to the process for the revision of the curriculum was the development of goals for change. These goals were developed from advisory committee recommendations. The advisory committee included departmental faculty, students, and alumni; faculty from other departments and universities; and industry representatives. The following three goals were identified:
- Improve on the existing strengths in the program.
- Provide opportunity for advanced skill de velopment that was viewed as a program strength in the 1992 Graduate Program Review Report.
- Develop concentrations that build on the strength of Appalachian's teaching tradition.
- Adapt to change.
- Expand the core of professional courses to address the development of specified core skills.
- Add a course, Research in Technology, for non-teaching majors.
- Add a graduate level course on Technology and Culture to address social and cultural implications for technology.
- Change the skill development course to emphasize the research and development process, including the concepts of invention, innovation, and development.
- Include the computer applications course in the core requirements.
- Prepare for the future.
- Promote core skills throughout the program that foster the development of graduates who can effectively interpret and manage the systems and products of technology by working effectively with others.
- Add concentrations for the Industrial Technology major that includes options for interdisciplinary course work.
Educational Objectives for Graduates
The core courses centered around developing and reinforcing specific skills and information from selected content areas. The goal was to prepare technologists either for teaching the concepts of technology education or working in industrial settings. This includes the understanding and application of technical skills in a variety of contexts with the ability to evaluate, synthesize, invent, and communicate this information effectively to others. Development of team skills and communication skills was considered critical in this process as well as direct and frequent contact with those currently working in education and/or industry.
Major concepts identified for the core classes and throughout the master's program are listed below:
- Technical literacy.
- Systems analysis.
- Technology transfer.
- Technology assessment/forecasting.
- Social and cultural impacts of technology.
- History of technology.
- Networking with industry and education: internships, visitations, speakers, training workshops, interviews, research in industries and schools.
- Strong communication skills: writing, speaking, listening, technical reports, presentation skills, computer skills, individual and group communication theory.
- Leadership and professional development: professional associations, conferences, workshops, administration skills.
- Research skills: statistical analysis.
- Problem-solving skills: the inventive process, design, creativity, scientific method, group skills.
- Management skills: coaching, team-building skills, management styles, work environments.
Challenges
Perhaps the biggest challenge in such an ambitious change to an existing program is gaining the support of others. Whereas undergraduate technical areas are under the direction of a small number of faculty, the graduate program spans all technical areas. All faculty needed to collaborate and have a voice in the direction of the graduate curriculum.
One of the challenges in gaining support from faculty within the department concerned the emphasis of the university on undergraduate education. Faculty in the department had a full load of undergraduate courses, and there was a continuing and growing demand for these undergraduate classes. Undergraduate courses traditionally have larger course enrollment than graduate courses. It was difficult to justify assigning a faculty member to teach a graduate class with five students when the same faculty member could teach an undergraduate class with 20 students.
The graduate program offered courses in specific technical areas that often had low enrollment but allowed graduate students to have close relationships with faculty in their technical areas. The opportunity for graduate students to work closely with faculty in developing advanced technical skills was recognized as a strength of the program by faculty, alumni, and students, but faculty were often overwhelmed by the individual instruction required of graduate students in addition to their regular course load.
A new course titled Technical Competency Development was conceptualized to allow students to update technical skills in their specific technical areas. This course replaced several advanced technical area courses that always had low enrollment. It could be repeated for additional credit. Fifty percent of the work in the class was in a structured graduate class meeting with a seminar format to cover the specific course topics and objectives. The remaining 50% of the work was based on an individual contract by each student for one of three options:
- Individual research and development in the student's technical area with their technical area advisor.
- Practical experiences in the student's technical area, either in industrial or educational settings.
- Students take a technical area course offered in the department in order to update technical skills that represent new/emerging technologies or in related/complementary technical areas.
There were several advantages for this course:
- Graduate students could work on a variety of problems in different technical areas. They have the opportunity to work in specific areas using faculty throughout the department as resources as well as contacts from industrial settings.
- Structured course activities include networking with graduate students through seminars emphasizing systems and processes that are related to all technical areas. Everyone learns from each others' activities.
- Graduate faculty have a reduced undergraduate load in order to teach a graduate class.
Other challenges existed due to the limited funding for the graduate program and the absence of a recognized reward and recognition for graduate faculty status. The support of the chair and dean for the revised graduate program and a commitment for recognizing graduate faculty status in promotion and tenure decisions, and a rotating reduction in undergraduate course loads for graduate faculty were clearly communicated to all faculty. Also faculty were continually provided with information about resources for graduate faculty through the graduate school for research, presentations, and the writing of articles. Priority for graduate assistant assignments was also given to faculty working with graduate students.
Networking Components of the Process
Throughout this process, technology faculty networked with other professionals. Faculty in the department met with faculty from other departments on campus to discuss interdisciplinary opportunities. Five interdisciplinary concentrations for the master of Industrial Technology degree were developed. These concentrations included selection of courses from 15 other departments on campus. Permission from these departments was needed for approval of the concentration options. For example, Technical Communications was an interdisciplinary concentration that included course options from the departments of Technology, English, Management, Curriculum and Instruction, and Decision Sciences, while the Appropriate Technology interdisciplinary concentration course options were from Technology, Anthropology's Sustainable Development Program, Biology, Geography, Political Science, and Sociology. Many departments were willing to work with us in developing these options. This provided a good opportunity to inform others on campus about our program areas in the Department of Technology and was, perhaps, part of the reason for the positive reception universitywide during the approval process of the final curriculum proposals.
Contacts outside the university were also instrumental in setting goals and establishing the direction for the revised curriculum. Correspondence with industrial personnel helped with suggestions for core skills in the program. Especially helpful were those involved in human resources, industrial training and educational programs, and management. The graduate courses emphasize networking with industry through practical experiences and internships. Guest speakers and field experiences are an integral part of the program.
Contacts with other universities, community colleges, technical schools, the public school system, and the State Department of Public Instruction also contributed suggestions for the graduate program.
Suggestions for core classes for teacher preparation were included in the revised curriculum.
Summary of Curriculum Changes
The curriculum changes involved the deletion of seven courses, the addition of seven courses, and changes to five courses. The graduate core of classes was expanded to include a computer skills course and a course addressing readings in technology and culture. A research class for industrial technology majors was added. Eight concentrations were developed for industrial technology majors. Technology concentrations were organized in two groups: interdisciplinary concentrations (Applied Electronics, Appropriate Technology, Industrial Technology, Technical Communications, Technical Training) and technology concentrations (Building Science, Graphic Arts and Imaging Technology, Manufacturing Technology).
The 1997-1999 Appalachian State University Graduate Bulletin provides the following description for the revised graduate curriculum:
The Department of Technology provides programs in the study of technology. The department offers courses in a variety of technical areas including: manufacturing, graphic arts and imaging technology, appropriate technology, electronics, drafting and design, photography, technology education and construction. The student has the opportunity to develop technical skills in selected areas. Skills and experiences gained in these areas are related to professional development in the student's selected field of endeavor.
The technology curriculum includes knowledge, concepts, and experiences which help the student interpret and manage the requirements of a technological society. Students will develop skills for understanding and effectively managing the systems and products of technology. Emphasis at the graduate level includes leadership, professional, and human relations skill development. A team based problemsolving approach to coursework and research is stressed. Practical experiences from industry and education are integrated into the core courses. The program's aim is to foster philosophies for lifelong learning and skills for being effective in environments involving continual change. Advanced technical skills are developed in relation to specific concentration areas.
Benefits of Collaboration
The benefits of collaboration when revising our graduate curriculum have surfaced in a variety of forms beyond the transformed courses and concentrations. Prior to this process it was difficult to motivate faculty to commit to applying and maintaining graduate faculty status, to participate in decision making regarding the graduate program, and to buy into the importance of the graduate program to the department. Since all departmental faculty had input and saw the interest of others outside the department during the revision of the program, the majority versus the minority now have a vested interest in graduate education. The majority of our faculty are now applying and maintaining graduate faculty status and are participating in teaching graduate courses and attending graduate committee meetings. The overall attitude and morale of the faculty have changed to reflect a deeper commitment to graduate education.
Dr. Wey is a Professor and Graduate Coordinator in the Department of Technology at Appalachian State University, Boone, North Carolina. Dr. Estepp is a Professor and Chair of the Department of Technology at Appalachian State University, Boone, North Carolina. He has received the Honorary's Laureate Citation. They are members of Gamma Epsilon Chapter of Epsilon Pi Tau.References
Buffer , J. (1979). Graduate education in industrial arts. In E. Martin (Ed.), Industrial arts education: Retrospect, prospect (American Council on Industrial Arts Education 28th yearbook). Bloomington: McKnight.
DeVore , P. (1991).The "why" of graduate study. In J.Wright (Ed.), The essential elements of a quality graduate technology education program (CTTE Monograph 12). Reston, VA: Council on Technology Teacher Education.
Jones , R. (1991). Curriculum development. In J. Wright (Ed.), The essential elements of a quality graduate technology education program (CTTE Monograph 12). Reston, VA: Council on Technology Teacher Education.
Maley , D. (1991). Instructional strategies at the graduate level. In J. Wright (Ed.), The essential elements of a quality graduate technology education program (CTTE Monograph 12). Reston, VA: Council on Technology Teacher Education.
Miller , P. W. (1984). Developing graduate research competencies in industrial education. Journal of Industrial Teacher Education , 21(2), 5467.
Page , W., Dugger, J., & Wolansky, W. (1996). Essential components of doctoral programs for industrial technology education. The Journal of Technology Studies , 12(2).
Scott , M., & Buffer, J., Jr. (1995). Undergraduate and graduate technology education. In E. Martin (Ed.), Foundations of technology education (CTTE 44th yearbook). New York: Glencoe.
Wey , B. (1992). Graduate program review . Boone, NC: Appalachian State University, Graduate School.
4. Anticipating Rescue 9-1-1 in a Mobile Wireless Society
by Tim Obermier
Wireless telephones provide us with security, mobility, and peace of mind in unexpected situations. Those who have wireless telephones, commonly referred to as cellular telephones, probably could not imagine a personal or professional life without such conveniences. These seemingly simple devices have helped rescue stranded motorists and alerted emergency personnel to countless accidents, in effect, saving numerous lives. They have also become the personal convenience and efficiency devices of this decade.
While the benefits are obvious, the cellular telephone is contributing to a societal evolution-the evolution towards a mobile wireless society. Satellite television, paging, data, and voice are all wireless services many of us depend upon. With the correct complement of wireless devices, one can roam the world in the most remote regions and still maintain contact. Several research expeditions have included thousands of individuals, all thanks to wireless technologies. One of the many implications of this newfound mobility is a societal demand for additional security and safety. As people use their cellular telephones to report accidents, spot hazardous weather, and ensure personal safety, the device takes on more importance than simply the novelty it once was. Cellular telephones are becoming so prevalent in our society that they are currently reshaping the way emergency personnel receive notification and respond to accidents and emergencies.
Evidence of the increasing importance of the cellular telephone, and the evolution in process, exists with the large numbers of people purchasing them. According to the Cellular Telecommunications Industry Association (CTIA), there are currently 68 million wireless subscribers in the United States ( Wheeler, 1999 ). Subscriptions for cellular telephones have increased at an average annual rate of 52% since the CTIA began keeping industry statistics in 1985 ( CTIA, n.d. ). According to a recent study conducted by the Consumer Electronics Manufacturers Association (CEMA), cellular telephones are in 39% of American households. Of those surveyed, 44% indicated that they purchased their cellular telephone to be able to communicate in an emergency ( CEMA, 1998 ).
The Problem
With the growth of wireless subscribers and an increasingly mobile society, emergency calls placed by cellular telephones are increasing. Dr. Bob Cobb, director of education for the National Emergency Number Association, places the total number of 9-1-1 wireless and wireline calls at approximately 260,000 per day ( personal communication, September 22, 1998 ). According to testimony before the U.S. House of Representatives speaking in favor of the Communications and Public Safety Act of 1999, Wheeler ( 1999 ) indicated that emergency 9-1-1 calls from cellular telephones total over 98,000 calls daily. In further testimony, it was noted that at least 35% of cellular telephone owners have used their telephones in an emergency or life-saving situation.
Wireline or landline telephones are those found in homes or businesses that are connected to the telephone network via copper wires to the local telephone office. Although the ever-popular portable telephones are wireless between the handset and base unit, the base unit must be connected to the wireline network. Portable telephones contribute to mobility, but only within the relatively short radius allowed by its base unit. The term cellphone or cellular telephone isused to refer to both forms of wireless telephones, analog cellular and digital personal communication system (PCS). The term cellphone has evolved from the theoretical engineering design of a cellular system that appears like a honeycomb or cell when drawn as a schematic.
Wireline telephone systems are static, and the geographic location of the telephone instrument is always known. Therefore, when an emergency call is placed to an enhanced 9-1-1 system through a wireline telephone, the Public Safety Answering Point (PSAP) can identify the name and street address of the caller. PSAPs are command centers from where 9-1-1 telephone operators dispatch appropriate emergency personnel in response to a need for emergency assistance. PSAPs are funded through monthly fees paid by everyone served by wireline 9-1-1 service. With the street address, PSAP operators can more efficiently dispatch assistance without first attempting to discern from the caller, who may have difficulty speaking, the street address where the assistance needs to be delivered.
While the mobility of a cellular telephone is the primary benefit, mobility becomes the most negative attribute of a cellular phone when seeking emergency assistance. Unlike wireline telephones, the location of cellular telephones can only be determined through interaction with the caller. With rapid subscriber growth of cellphones and a subsequent increase in the number of wireless 9-1-1 calls, PSAP operators are finding it extremely difficult to determine the location of mobile wireless callers. Individuals have died attempting to describe their location. In one specific incident in Nebraska, an individual was routed through three separate PSAPs until an operator who used to live in the area finally recognized the surroundings a heart attack victim was describing. Unfortunately, emergency services arrived too late and the individual did not survive. Cellular telephones are mobile, and identifying their location is difficult at best. Compounding the location problem, not all of the geographic United States is served with the most basic 9-1-1 service; therefore, cellular telephones do not always reach emergency services by dialing 9-1-1.
As society becomes more mobile, demand is increasing for wireless cellular telephones to have the same technological features as wireline telephones. A call to an enhanced 9-1-1 system from a wireline telephone will result in the arrival of emergency personnel even if the caller cannot speak to the operator. A call to 9-1-1 on a cellular telephone will result in a time-consuming explanation of the caller's location because callers are not always aware of their whereabouts and must describe local landmarks or roadways to identify their location. Should the wireless caller be unable to speak, emergency services are unlikely to arrive. To be functionally equivalent to a wireline telephone, the cellphone requires the technological ability to automatically be located. The location information must then be transmitted to a PSAP for emergency dispatch.
In some instances, wireless carriers, the equivalent of your local telephone company for cellular telephones, block wireless 9-1-1 calls, leaving callers at a complete loss for emergency services. Blocking is a process of rejecting any 9-1-1 call placed on the wireless system. Blocking occurs because either the PSAP will not accept the wireless call load due to lack of funding or the wireless carrier lacks the technology to pass the call to the PSAP. Unfortunately, wireless carriers also block 9-1-1 calls due to concerns of liability. Several wireless carriers have been sued for incidents where wireless emergency calls did not reach 9-1-1 PSAPs. Because the wireless system is considered to be a competitive industry, ancillary to the wireline industry, wireless companies do not receive protection from liability like wireline carriers. In the case of 9-1-1 wireless call blocking, mobile individuals who need emergency services have to be aware of special dialing codes or local emergency numbers to receive assistance.
Travelers unaware of 9-1-1 blocking and lacking local seven-digit emergency telephone numbers are essentially stranded. Representative Pat Danner found that travelers had to dial *55 in Missouri, *999 in Illinois, *DUI in Ohio, and *77 in Maryland to access emergency services ( Wheeler, 1999 ). Further analysis reveals that at least 15 different numbers exist across the United States to access emergency services from cellular telephones.
If the cellular telephone is to be a truly effective tool for a mobile society, all wireless carriers must contend with the challenge of creating a wireless enhanced 9-1-1 system that ensures consumers will experience the same benefits and quality as wireline telephones. The wireline 9-1-1 system has evolved into a high quality, life-saving technology that society now relies upon daily for safety and security.
History of Basic 9-1-1 Service
Before the technological development of dial tone and direct dial technology, a person initiating a telephone call had to use a central exchange operator who immediately connected the customer's call to the appropriate emergency service. Because of the technological design limitations of the telephone system, operators were typically local individuals familiar with most local residents. In time of emergency, they could locate doctors, firefighters, or police, whether on duty or not.
The development of dial tone and direct dialing technology allowed users to dial their own connections, resulting in a consolidation of operator services. No longer was the extensive number of local operators required. Dialing "0" could result in contact with an operator quite unfamiliar with the caller's town or area. Operators might even be several hundred miles away. To reach local emergency personnel, one had to know the specific telephone number for fire, police, or doctors, or know where to look for the directory listing. This could be a difficult and untimely task should a house be burning or a medical emergency be affecting a person's presence of mind.
President Lyndon Johnson's Commission on Law Enforcement and Administration of Justice Report ( The President's Commission, 1967 ) first recommended the creation of a single emergency phone number. A year later, AT&T announced its decision to make 9-1-1 a universal emergency number for all their local telephone exchanges. AT&T's announcement in 1968 created a universal emergency number that telephone companies began to adopt.
Burton ( 1996 ) therorized that AT&T spent large amounts of money to support emergency services through their operators. The concept of 9-1-1 may have been created by AT&T to shift the burden of providing operator services for emergency connections from AT&T to public safety agencies, thus allowing for cost savings and creating future equipment sales. While basic 9-1-1 service greatly enhanced emergency services, it was soon to be replaced due to severe limitations.
Wireline Enhanced 9-1-1
Basic wireline 9-1-1 allows for emergency calls to be routed to PSAPs by the local telephone company, rather than first going through an operator or dialing a seven-digit phone number. The PSAP then dispatches the appropriate emergency personnel. In systems with basic 9-1-1 service, the PSAP operator does not receive two critical pieces of information: the seven-digit telephone number of the calling party and the location of that party.
Wireline enhanced 9-1-1 (E 9-1-1) service provides to the PSAP operator the caller's telephone number and location. The caller's telephone number is displayed on the PSAP operator's computer monitor through automatic number identification (ANI), and the street address is displayed through automatic location information (ALI). The ALI allows PSAP operators to coordinate the caller's location with the geographically closest emergency services. ALI ensures that callers who cannot speak, or who may lose consciousness after dialing, can still receive emergency services. ANI enables PSAP operators to call a person back should they hang up prematurely or in case of a disconnected call.
Nearly 85% of the population and 50% of the geographical area of the United States have access to some form of 9-1-1. Of that coverage 95% are served by E 9-1-1 ( National Emergency Number Association, 1998 ). Wireline telephones that benefit from E 9-1-1 allow PSAPs to become much more effective at serving the emergency needs of their constituency. Wireline telephone customers currently rely on a standard of excellent service that remains to be duplicated in the world of cellular telephones.
The Federal Communication Commission (FCC) has recognized the importance and quality of wireline E 9-1-1, the tremendous growth of wireless subscribers, and the need for ubiquitous E 9-1-1 coverage, for both wireline and wireless. On July 26, 1996, the FCC set forth in CC Docket 94-102 initial rules and regulations for the implementation of Wireless Enhanced 9-1-1 (WE 9-1-1) service.
Societal demand helped to begin the transition to WE 9-1-1; however, regulatory pressure was required to begin implementation of what the public both needs and wants. As with any societal transition, several regulatory, technological, and societal obstacles must yet be surmounted before cellular telephones become the personal security and safety device of an evolving mobile society. Regulatory, Technological, and
Societal Obstacles
Wireless enhanced 9-1-1.
Because of the FCC ruling, WE 9-1-1 should eventually become a reality; however, the FCC ruling contains several provisional mandates. First, the PSAP must be capable of receiving and using the ALI and ANI information transmitted to them by the wireless service provider. Second, the PSAP must formally request the service provider to send the ALI and ANI to the PSAP. Third, there must be a system in place to reimburse the wireless service providers and the PSAP for the cost to deploy and maintain the technology to make the service possible.
According to the FCC ruling, deployment of WE 9-1-1 will occur in two phases. Phase I requires the wireless caller's phone number and the specific cell site or sector identification number to be transmitted to a PSAP. Therefore, when a caller makes an emergency call from his or her cellular telephone, the 9-1-1 operator will receive a display on his or her computer monitor of the cellular 10-digit telephone number and the cell site location from which the call originated. If the emergency call is disconnected, this information will allow the operator to reconnect the caller. It will also allow the operator to have initial broad-based location information to assist in identifying the caller's location. In larger metropolitan areas, the ANI combined with the ALI will allow selective routing (SR) to take place. SR ensures that the PSAP and subsequent emergency services nearest the caller's location will receive the call. The April 1, 1998, deadline for Phase I was subject, however, to provisional FCC mandates. Wireless service providers are not subject to the federal mandates if the PSAP cannot use the data and if the PSAP failed to file a formal request to the wireless service provider. In addition, wireless service providers are not obligated to provide WE 9-1-1 services should a funding mechanism not be in place.
Phase II of the FCC ruling requires all wireless service providers to transmit to the PSAP the longitude and latitude of all wireless 9-1-1 callers within 125 meters by October 1, 2001. The location accuracy must be completed successfully at least 67% of the time. During an emergency call, the ANI and ALI must be transmitted to the PSAP within a fraction of a second. Therefore, when callers cannot speak or are completely unaware of their location, they can dial 9-1-1 with their cellular telephone and the PSAP will locate them, directing emergency personnel to the site. Advancing to the next technological step, rescuers could utilize global positioning with longitude and latitude data to locate individuals with pinpoint accuracy. This would eliminate all the guesswork in the location of persons needing emergency assistance. It is important to note that currently altitude is not a consideration for location. Therefore, if a person was in a multiple-story building, location identification could be more complicated. The FCC has sought comments on the issue of altitude, but it has not ruled on the topic as of yet ( FCC, 1996 ).
Another recent decision by the FCC may have a tremendous impact upon the wireless consumer who only wants a cellular telephone for emergency purposes. In a Memorandum Opinion and Order adopted by the FCC on December 1, 1997, the FCC announced that wireless carriers must route all wireless 9-1-1 calls to a PSAP without validation of a subscriber's account ( FCC, 1997 ). This decision allows any working cellular telephone, regardless of subscriber account status, to transmit a 9-1-1 call. This ruling is significant because as consumers upgraded to models with more features and benefits, older cellular telephones were discarded. Previously unusable and without value, they now can be used for emergency purposes.
Technological strategies are primarily in the testing phase to meet the FCC WE 9-1-1 mandates. However, regardless of technological deployment, consumers will not receive the benefit of WE 9-1-1 unless three major issues are resolved: Each state must have state funding, liability protection for wireless carriers, and an organized process for antenna tower location.
State funding, liablility, and antenna tower siting.
Monthly wireline telephone bills include a fee for 9-1-1 service. Legislative or regulatory statutes establish the authority to collect fees to support the 9-1-1 system. The fee supports technology deployment and maintenance by the local telephone company to route emergency calls to the PSAP. Support also includes PSAP technology deployment and maintenance. Currently, in states where WE 9-1-1 funding statutes do not exist, wireless subscribers do not pay a monthly levy and therefore do not contribute funds to keep the wireline E 9-1-1 system operational. In states without funding legislation, the call load placed upon PSAPs by wireless subscribers lacks financial support.
The problem with funding rests with the mobility of a cellular telephone. Since a wireline telephone is not mobile, it is very easy to determine which PSAP should receive the monthly payment to the 9-1-1 system. However, a cellular telephone could quite literally be anywhere in the country when placing an emergency call. Which PSAP then is to receive reimbursement for processing the wireless 9-1-1 call and how does the PSAP receive reimbursement? The answer presumably lies with establishing a WE 9-1-1 fund administered by each state's public service commission (PSC) or public utility commission (PUC). The PSC or PUC would then reimburse PSAPs for the volume of calls they receive from wireless callers. Currently, according to XYPoint ( 1998 ), 34 states have funding mechanisms in place. Of the 16 that do not, only one has legislation pending at this time.
Once states pass funding statutes, one would assume that WE 9-1-1 service could begin. For wireless carriers there yet remains an issue that has caused WE 9-1-1 deployment delays for several states. Wireline telephone companies receive governmental immunity from liability as determined by statute or regulatory authority. Currently, many states do not grant this same immunity from liability to wireless carriers. With no immunity from lawsuit, a wireless carrier has the potential of liability for any mishandled WE 9-1-1 call. Wireless carriers are concerned about liability due to the possibility of dropped calls and gaps in coverage. As mentioned previously, only 50% of the geographic area of the United States has 9-1-1 coverage. Should an emergency caller not be able to complete a call, the carrier is potentially liable for the failed connection. Currently, only 30 states have legislation protecting wireless carriers from liability for providing WE 9-1-1 service ( XYPoint, 1998 ). In those states without protection from liability for wireless carriers, WE 9-1-1 service will be delayed, or possibly not implemented at all.
When funding and liability issues are resolved, there yet remains the issue of tower siting. The Telecommunications Act of 1996 mandates that any state or local government: "(I) shall not unreasonably discriminate among providers of functionally equivalent services; and (II) shall not prohibit or have the effect of prohibiting the provision of personal wireless services." State and local governments also cannot deny tower applications based on environmental effects of radio frequency emissions ( Knauer, Machtley, & Lynch, 1996 ). In a recent court decision by the Fourth Circuit U.S. Court of Appeals, the court provided an interpretation of the Telecommunications Act of 1996. The judges ruled that applications for erecting a cellular antenna tower could be rejected based on citizen opposition ( Warner, 1998 ). This creates an awkward position for wireless carriers since the lack of antenna towers means lack of coverage area for WE 9-1-1 service. In essence, by denying tower location applications, citizen opposition creates limitations in the service for which they most often purchase cellular telephones.
Once a solution to the politics of funding, immunity from liability, and tower locations are finally resolved, the wireless carrier must decide upon location technology that will satisfy Phase II of FCC Docket CC 94-102. The technology deployed will ultimately determine if existing wireless handsets will serve callers in an emergency, or if new handsets will have to be purchased that contain updated technology.
Location technology and privacy.
The two location technology solutions are (a) solutions involving the subscriber's cellular telephone and (b) solutions involving changes to the wireless carrier's network. Solutions involving changes to cellphones are a disadvantage to subscribers because they will then require new cellphones to take advantage of WE 9-1-1 service. Network solutions will allow existing cellphones to take advantage of WE 9-1-1. Regardless of the solution selected by wireless carriers, a major problem for subscribers emerges as each company selects differing solutions. A company in one part of the country may use a cellphone solution and another company in another geographic area may implement a network solution.
There are three primary methods to accomplish location of wireless callers: (a) time difference of arrival (TDOA), (b) angle of arrival (AOA), and (c) global positioning system ( GPS; Dziatkiewicz, 1998 ). TDOA and AOA are network solutions that will work with millions of existing cellular telephones. GPS, however, requires the customer to purchase a new cellular telephone.
TDOA analyzes the slight time delays from the cellphone radio signal as experienced from several different cell towers. This process triangulates the position of the caller through a process called hyperbolic trilateration. AOA analyzes location through a sophisticated antenna array added to cell sites. The array determines the direction from which a cellphone is entering a cell site territory. Utilization of two cell sites and the cellphone itself triangulates the position of the caller. A GPS solution operates from the array of GPS satellites used for all GPS receivers. While GPS may appear to be the best choice, this solution would require new cellphones for the service to work. Customers with a desire to benefit from this solution would have to replace their cellphones.
All three of the location technologies create privacy concerns. TDOA allows the continuous tracking of the location of a cellular phone. AOA can trace in continuous intermittent mode. GPS technology can also be adapted to operate in an intermittent mode. The location technology that enables the benefits of WE 9-1-1 complicates the societal issue of personal privacy. Since location technologies allow for continuous tracking second by second, location data could be collected and sold to marketing firms. Data could be specific to a customer or aggregated as a whole. For example, local supermarkets could offer free local cellular telephone service while shopping. Since tracking would occur whether the cellular telephone is used for a call or not, customers would be tracked continuously, building a marketing database regarding each individual's shopping patterns. Location technology could also be used to find lawbreakers, corroborate legal testimony, or ultimately track your children on a Saturday night. Fortunately, cellular telephones are under development that would only release location information when the caller dials 9-1-1, allowing for customer privacy.
Conclusion
Once WE 9-1-1 is fully implemented and the regulatory, technological, and societal obstacles are resolved, additional lives will be saved, travelers can feel more at ease, commuters may feel a little safer, and parents may not worry as much. When compared to the regulatory and societal concerns, the development of technology to make the system work seems to be a relatively small problem for WE 9-1-1 implementation. Once these issues are resolved, cellular telephone consumers should finally have a service that will truly benefit a mobile wireless society.
Dr. Tim Obermier is an Assistant Professor of Telecommunications Management at the University of Nebraska at Kearney. He is a member of the Omega Chapter of Epsilon Pi Tau.References
Burton , A. (1996). 9-1-1. DISPATCH Monthly Magazine . Retrieved September 24, 1998 from the World Wide Web: http://www.911dispatch.com/911_file/911_burton.html
Cellular Telecommunications Industry Association. (n.d.). Wireless subscribership: December 1985December 1998 . Washington, DC: Author. Retrieved August 18, 1999 from the World Wide Web: http://www.wow-com.com/images/1298datasurvey3.gif
Consumer Electronics Manufacturers Association. (1998, February 11). Multiple wireless phone families on the rise . Arlington, VA: Author. Retrieved September 18, 1998 from the World Wide Web: http://www.cemacity.org/gazette/files2/wrlsphone.htm
Dziatkiewicz , M. (1998, September 21). Vendors work to perfect E9-1-1 location solutions. Wireless Week , p. 50.
Federal Communications Commission. (1996, July 26). Revision of the commission's rules to ensure compatibility with enhanced 9-1-1 emergency calling systems (CC Docket No. 94-102). Washington, DC: Author. Retrieved September 28, 1998 from the World Wide Web: http://www.fcc.gov/Bureaus/Wireless/Orders/1996/fcc96264.txt
Federal Communications Commission. (1997, December 23). Revision of the commission's rules to ensure compatibility with enhanced 9-1-1 emergency calling systems (CC Docket No. 94-102). Washington, DC: Author. Retrieved September 29, 1998 from the World Wide Web: http://www.fcc.gov/Bureaus/Common_Carrier/Orders/1997/fcc97402.txt
Knauer , L. T., Machtley, R. K., & Lynch, T. M. (1996). Appendix 1: The Telecommunications Act of 1996. In Telecommunications Act handbook (pp.171290) . Rockville, MD: Government Institutes.
National Emergency Number Association. (1998, March 18). The development of 9-1-1 . Columbus, OH: Author. Retrieved September 28, 1998 from the World Wide Web: http://www.nena9-1-1.org/History%20of%20NENA%20and%20911/history3.htm [note -- this link is no longer valid]
The President's Commission on Law Enforcement and Administration of Justice. (1967, February). The challenge of crime in a free society . Washington, DC: U.S. Government Printing Office.
Warner , E. (1998, September 28). Federal court ruling a setback to antenna siting. Wireless Week , p. 64.
Wheeler , T. E. (1999, February 3). Testimony of CTIA President Tom Wheeler before the House Subcommittee on Telecommunications, Trade, and Consumer Protection on the Wireless Communications and Public Safety Enhancement Act of 1999. Washington, DC: Cellular Telecommunications Industry Association . Retrieved February 10, 1999 from the World Wide Web: http://www.wow-com.com/lawpol/congress/pdf/tew2399.pdf
XYPoint . (1998, August 27). Master chart of state E9-1-1 treatment . Seattle, WA: Author. Retrieved September 30, 1998 from the World Wide Web: http://www.xypoint.com/legislation/we911statutes.html

TS